If you need any help configuring the following steps, be sure to get in touch: info@vizito.be or via chat.
The AD integration is configured by using the Vizito AD client which needs to be installed on a device/server which the tablet can connect to. So the tablet needs to be able to communicate to this device/server via its network.
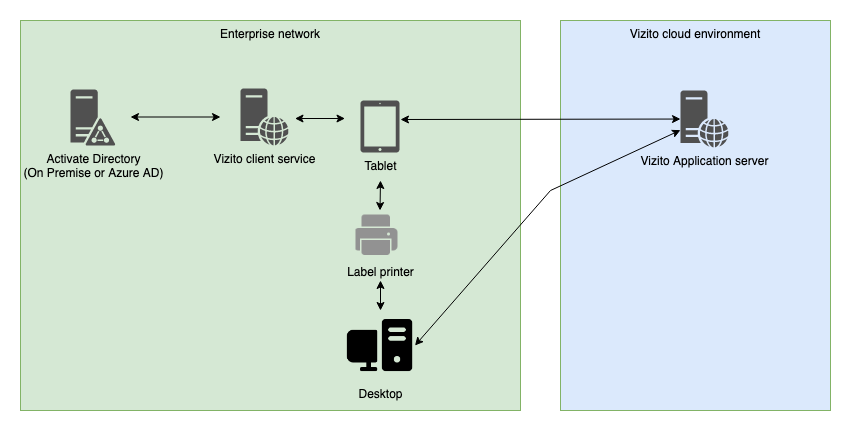
Please find a schematic representation below:
Step 1: NodeJS
Download and install the latest version of NodeJS from the NodeJS website.
Step 2: Vizito AD client
Download and extract our Vizito AD client to a folder of your choice
Step 3: Config
Edit config.json to match your environment.
Here you can find the configuration values and a description of what information you need to enter:
| JSON property | Mandatory | Description |
|---|---|---|
| ldap*url | Yes | The internal URL / IP of your LDAP server. Example: _ldap://ldap.forumsys.com .* |
| ldap*bind_credentials.user_cn | Yes | The user CN that is used for the LDAP bind. Usually a specific technical user is created for this with read only rights. |
| ldap_bind_credentials.password | Yes | The password for the LDAP bind user. |
| search_scope | Yes | This configures the search depth: _base* - searches only the searchbase level; _one - searches only the immediate subordinates to the base object, but does not include the base object itself; sub - this searches the search*base level and all of its subtrees. |
| search*base | Yes | The search base used for looking up CN entries. This should be the top level of your LDAP domain where you want to look for entries. |
| mobile_prefix | No | If your LDAP dictionary contains local or internal mobile phone numbers (without country code), you can add a prefix containing the country code. The first character of the local or internal mobile phone number will be replaced with this prefix. |
| ldap_filter | No | If you want to filter the LDAP search results, you can do so using an ldap filter. This searches only for matching records. |
| Examples of this filter are: only persons belonging to a specific group, only persons having a mobile phone number configured, … . | ||
| An example of a filter: *(&(memberof=OU=VizitoGroup,OU=Applications,OU=Groups,DC=company,DC=com))* . | ||
| api*port | Yes | Default value: _48800*. This configures the port at which the node application will listen for HTTP(s) requests. |
| use*ssl_for_api | Yes | Default value: _false*. If set to _true_, it will use the ssl.ca, ssl.key and ssl.cert configuration items to load a private key / public key pair for enabling TLS communication. |
| Read up on creating your own self-signed certificates using a custom root CA. | ||
| authentication.enabled | Yes | Indicates if basic authentication is needed to make a request to this server. |
| authentication.username | No | The username that is configured for basic authentication. |
| authentication.password | No | The password that is configured for basic authentication. |
Step 4: Run
Navigate to the folder where your ldap client resides, and run
- “npm install” (only required once)
- “node server.js”
If everything works as intended, you should see “Server is listening”
You can now use a browser to test the LDAP http server by pointing your browser to
http://ip_or_hostname_of_machine_running_ldap_client:48800/(change the port if you changed it in the config file) If your browser shows a JSON object representing the users you want to expose, than everything works!
Step 5: Configure the backoffice to make the tablet connect to the client
Navigate to the Vizito backoffice and under Settings, configure the Host datasource as ‘Managed externally’ and fill in the Integration URL.
An example: http://192.168.1.100:48800.
Now the tablet will look up the information from the installed client.
Step 6: Use PM2 to daemonize the node process
Please refer to PM2 manual for instructions on how to install and use PM2.
Troubleshooting
Demo services are available for testing purposes. They include names such as “Tesla”, “Newton”, etc..
- HTTP version:
http://178.162.136.223:48800 - HTTPS version:
https://source.vizito.eu:48801
If you’re using a HTTPS configuration you can configure multiple CA references. Add each CA between " (quotes) in the CA array, which you can find in the config.JSON file.